The $Strategy Strategy Proliferation
We're observing a rapid proliferation of the "$Strategy Strategy," where companies adopt Bitcoin aiming for premium valuations by aggressively raising capital to increase Bitcoin-per-share, a high-risk approach we anticipate will lead to industry consolidation under market pressures.
“Nothing in biology makes sense except in the light of evolution.”
-Theodosius Dobzhansky
Key Takeaways
The next phase in Bitcoin’s evolution is here: corporate adoption on balance sheets. As of May 2025, 199 entities collectively hold 3.01 million BTC ($315 billion), and these numbers are rapidly accelerating.
Companies whose primary purpose is to hold Bitcoin will be valued as Bitcoin holding companies, similar to Strategy. To survive, these firms must command a premium known as the Multiple on Net Asset Value (MNAV) – the most important metric to track.
The MNAV premium hinges on trust in and execution by the core team. These teams must execute the Strategy playbook of raising capital through debt, stock issuance, and reinvesting cash flow to increase the amount of BTC held per share. New entrants are expanding on this approach.
The existential threat is an extended bear market that erodes the MNAV premium just as sizable debt maturities come due. New treasury companies face this risk even more acutely as they will have to raise capital on tougher terms and at higher leverage ratios than Strategy.
When failures inevitably hit, the strongest players are likely to acquire distressed companies and consolidate the industry. Fortunately, contagion risk is muted because most financing is equity-based; however, companies that rely heavily on debt pose a greater systemic threat.
The Next Evolution: Corporate Adoption
We have all witnessed Bitcoin’s rise over the past few years. Beyond the rise in price, adoption and recognition have crossed the chasm. Pivotal moments include El Salvador recognizing BTC as legal tender in September 2021, BlackRock launching the IBIT ETF in January 2024, the U.S. president emphasizing BTC as a strategic economic focus, and, as of summer 2025, a surge in corporate adoption of BTC on balance sheets.
According to Bitcointreasuries.net, 199 entities collectively hold 3.01 million BTC ($315 billion). Among these, 147 private and public companies account for 1.1 million BTC ($115 billion).
Recently, a wave of companies announced new Bitcoin treasury strategies. These range from firms diversifying their balance sheets with BTC to dedicated BTC treasury holding companies. These entities span diverse geographies and sectors, and they are led by reputable teams.
Since the start of 2024, the amount of BTC held by entities has more than doubled. Strategy accounts for 53% of the BTC held by corporations, with over 580,000 BTC. Other notable companies holding more than 10,000 BTC include Block.one (164,000), Tether (100,500), MARA Holdings (49,140), Twenty One (31,500), Riot Platforms (19,200), Galaxy Digital (12,800), CleanSpark (12,100), Tesla (11,500), and Hut 8 (10,300).
Thanks to its size, reputation, and lindy, Strategy is all but guaranteed to remain the leading BTC holding company. However, it is significant that the Strategy strategy is now being emulated. The growing number of companies adopting BTC on their balance sheets—and the rise of pure-play BTC treasury holding firms—has massive implications for Bitcoin.
How It Works And How To Value
Companies that simply add BTC to their balance sheets while continuing to focus on their core businesses will primarily be valued based on those core operations. The dynamic changes when a company's sole purpose becomes BTC holding—effectively opting to be valued based on the Bitcoin held.
To attract investors to buy their stock rather than just holding BTC directly, these companies must outperform Bitcoin itself. This outperformance is referred to as a premium called MNAV (Multiple on Net Asset Value).
For example, Strategy holds 580,250 BTC, worth approximately $60 billion, while its market capitalization stands at $104 billion—resulting in an MNAV of 1.7x. MNAVs can vary widely depending on factors such as company size, tenure in the market, alternative business lines, and more. Nonetheless, Strategy’s historical 2x MNAV is the long-term gold standard.
The market does not award a company MNAV simply because it owns Bitcoin. It does so when investors believe that management can reliably grow BTC-per-share faster than they could on their own.
Strategy has proven this by repeatedly executing on three capital levers since 2020:
Convertible Debt – Issue low-coupon senior notes that convert to equity only if the share price rises 30–50% above the issue date. This enables large, low-interest borrows while protecting dilution unless performance warrants it.
At-the-Market Stock Issuance – Maintain an ongoing ATM program to sell new shares when the stock trades above MNAV—effectively dollar-cost averaging into more BTC.
Operating-Cash Reinvestment – Redirect every dollar of free cash flow from the legacy business into buying spot BTC.
Second movers are adopting and iterating on this playbook. Some innovations include enabling BTC holders to swap coins for stock without triggering capital gains, acquiring businesses trading below net cash to convert value into BTC, acquiring distressed Bitcoin litigation claims, leveraging media and events, raising capital through PIPE (private investment in public equity) deals, and exploiting regulatory arbitrage.
Who Are The Players
Through the first half of 2025, more than 40 companies have publicly announced plans to adopt Bitcoin on their balance sheets, collectively raising tens of billions of dollars to execute these strategies.
These announcements vary widely – across industries, geographic regions, execution models, and the paths companies have taken to go public.
Notable names include Metaplanet (Japan), one of the earliest international adopters capitalizing on Japan’s ultra-low interest rates; Semler Scientific and GameStop in the U.S., whose treasury pivots have drawn significant mainstream attention; purpose-built entrants like Twenty One Capital, backed by Tether and Cantor; and firms like Strive and Nakamoto, which have leveraged reverse mergers to go public quickly.
See the slide above for a broader snapshot of companies that have announced Bitcoin treasury strategies as of May 2025.
Is It Sustainable
Nothing in finance is bulletproof – especially Bitcoin treasury companies.
Strategy endured a severe stress test during the 2022–23 bear market: BTC fell 80%, the MNAV premium collapsed, and access to fresh capital vanished. The company survived, though Saylor likely had some sleepless nights.
The existential threat is an extended bear market that erodes the MNAV premium just as sizable debt maturities come due. If the stock trades at or below NAV and lenders refuse to refinance, Strategy may be forced to liquidate Bitcoin to meet its obligations – triggering a reflexive death spiral of falling prices and further forced sales.
New treasury companies face this risk even more acutely. Without Strategy’s scale, reputation, and passive index inflows, they will likely raise capital on tougher terms and at higher leverage ratios. In a downturn, those aggressive structures could accelerate margin calls and distressed BTC sales, amplifying downside pressure across the market.
Where We Go From Here
The proliferation of Bitcoin treasury companies is still in its early innings; however, the crypto treasury model is already expanding into other crypto assets – Solana has DeFi Development Corp (valued at $100 million and holding more than 420,000 SOL), Upexi, and Sol Strategies, and Ethereum has SharpLink Gaming, which raised $425 million in a round led by Consensys. We expect more companies around the world to adopt this playbook, extending to more assets and taking on greater leverage to chase success.
Most will fail. Fortunately, contagion risk is muted because most financing is equity-based. However, companies that rely heavily on debt pose a greater systemic threat. When failures inevitably hit, the strongest players are likely to acquire distressed assets and consolidate the industry.
Ultimately, only a select few companies will sustain a lasting MNAV premium. They will earn it through strong leadership, disciplined execution, savvy marketing, and distinctive strategies that continue to grow Bitcoin-per-share regardless of broader market fluctuations.
Decentralized AI: An Investment Thesis by Breed
After a significant deep dive into the intersection of AI x Crypto. We’ve released our thoughts on the leading innovators in the space and potential applications of this groundbreaking technology stack.
In the burgeoning intersection of artificial intelligence (AI) and blockchain technology, Decentralized AI (DeAI) emerges as a transformative force, poised to redefine the paradigms of AI development, deployment, and governance. Breed recognizes DeAI's potential to democratize AI, ensuring its development is not only the purview of tech conglomerates but accessible to a broader community. This investment thesis explores the conceptual underpinnings of DeAI, its strategic importance, the synergy with crypto, and leading innovators in the space.
A World Without Decentralized AI
Conceptual Foundation of Decentralized AI
Decentralized AI stands at the confluence of AI and crypto, offering a radical departure from centralized models that dominate today's AI landscape. By distributing AI's computational and developmental processes across decentralized networks, DeAI not only democratizes innovation but also enhances data security and operational transparency. This paradigm shift, underpinned by cryptography, crypto economic primitives and smart contract functionalities, promises a future where AI technologies are developed in a more open, collaborative, and ethical manner.
Blockchain x AI: Pioneering the Future of Technology Synergy
The fusion of blockchain and AI will revolutionize how we all utilize AI, creating a synergy that leverages the strengths of both domains. This union brings forth a novel paradigm where blockchain's secure, immutable ledger and consensus mechanisms serve as the bedrock for AI systems. This integration ensures the authenticity and reliability of data used by AI, establishing a foundation where AI can operate on principles of security, transparency, and immutability. Such a robust environment is pivotal for AI to evolve and be trusted, especially in critical applications.
Combatting Centralization with Decentralized AI
In the current landscape, where a few tech giants hold sway over AI development, Decentralized AI (DeAI) emerges as a game-changer. It challenges the status quo by distributing AI development across a broad network, diluting the concentration of power and control. This decentralized model not only democratizes AI development but also fosters innovation and equal access. By breaking the monopolistic hold of big tech, DeAI paves the way for a more distributed and inclusive AI ecosystem, where different voices and perspectives contribute to the AI evolution.
Enhancing Security and Privacy
In an era where data breaches and privacy concerns are rampant, the amalgamation of blockchain and AI presents a powerful solution. By harnessing blockchain and cryptographic technologies, DeAI creates a secure framework for AI operations. This approach safeguards data transactions and AI model interactions, enhancing user privacy and building trust in AI systems. The blockchain backbone in DeAI ensures that data integrity is maintained, providing a more reliable and secure platform for AI development and deployment.
Navigating Regulatory Complexity with Decentralized AI
One of the most significant advantages of DeAI is its ability to transcend geographical and regulatory boundaries. Unlike traditional AI systems that might be hampered by regional regulations and constraints, DeAI operates on a global scale, unrestricted by local legislations. This global approach not only accelerates innovation but also ensures the development of AI applications that are diverse, inclusive, and universally applicable. In a world where AI's could be shackled by regulatory complexities, DeAI offers a pathway to unbridled innovation, fostering AI systems that are adaptable and versatile across different regions and cultures.
Leading Innovators in the Decentralized AI Space
Our analysis identifies key players and projects that are pioneering the DeAI landscape: (this space evolves everyday and this in no way exhaustive, please DM if we missed something)
1. Decentralized Compute and AI Inference Platforms
Overview: Combines platforms providing distributed computational power with those specializing in decentralized AI inference and compute. This category includes companies that break new ground in AI training capabilities and those addressing privacy and censorship in AI model inference.
Companies: Ritual, Akash, Render, Bittensor, io.net, Hyperbolic, Gensyn, Prime Intellect, Inference Labs, Lumino, Lilypad, Morpheus, Prodia, Hyperspace, Vanna, Arbius, Naptha
2. AI Data and Model Provenance
Overview: Focuses on decentralized, data ownership, governance and transparency of AI content. This category encompasses projects ensuring ethical AI development, data sovereignty, and content provenance.
Companies: Rainfall, Numbers, Grass
3. Token Incentivized AI Applications
Overview: Projects that use crypto tokens to drive engagement in AI-centric applications and enhance AI workflows, including companion apps and machine learning operations.
Companies: MyShell, Deva, Prodia, Arbius, ImgnAI, MyPeach
4. On-Chain AI Agents and Security
Overview: Develops AI agents that operate on blockchain, offering payment solutions and platform risk reduction. Also includes projects focused on on-chain verification of AI models.
Companies: AI Arena, Operator.io, Fetch.ai, Modulus Labs, Delysium, Agent Protocol, Morpheus, Mamoru, Autonolas, Test Machine
5. AI-Driven Blockchain Marketplaces and Learning Platforms
Overview: Creates decentralized marketplaces for AI algorithms and datasets, and federated learning initiatives. This category promotes collaborative AI development while respecting user privacy.
Companies: Bagel Network, SingularityNET, FedML (open source), DynamoFL (web 2), ManyAI, Numerai, Bittensor
6. Model Verification:
Overview: Projects that utilizes crypto technology (zero-knowledge- zk) to verify which models have done what they say they have done onchain.
Companies: Modulus, Giza, EZKL
Conclusion
Breed VC views Decentralized AI as a cornerstone of the next evolution in AI development. By championing a model that is secure, transparent, and distributed, DeAI aligns with our investment philosophy that values innovation, community, and decentralization. As we continue to explore investment opportunities in this space, our focus will be on projects that not only demonstrate technological excellence but also embody the principles of decentralization, contribute to the democratization of AI, and navigate the complex regulatory environment with a forward-thinking approach. The integration of token economies within these ecosystems further solidifies our belief in the potential of DeAI to create sustainable, impactful, and transformative AI technologies for the future.
A Closer Look at Breed VC’s Due Diligence Approach
We’ve developed a nuanced evaluation framework that aims to reduce risks while uncovering opportunities. This guide is intended to help startup founders understand what we’re looking for and why we consider each aspect important.
Guiding Early-Stage Crypto Founders
Due diligence is crucial for any investment, but it’s especially vital in the high-stakes, rapidly evolving world of early-stage crypto ventures. At Breed, we don’t claim to have all the answers. Instead, we’ve developed a nuanced evaluation framework that aims to reduce risks while uncovering opportunities. This guide is intended to help startup founders understand what we’re looking for and why we consider each aspect important.
Knowledge is Power
Insight 1: Evolving with the Times — A Modern Approach to Crypto Due Diligence
The blockchain and crypto industries are redefining how we think about finance and decentralized technology. This necessitates a fresh approach to due diligence, one that evolves alongside the technology itself. In our view, due diligence in this sphere needs to be as dynamic and adaptable as the market it serves.
The Dynamic Crypto Landscape: The crypto world isn’t just about currencies anymore; it encompasses a range of assets and technologies. Our due diligence adapts to these diverse types of opportunities, considering both their unique attributes and universal business principles.
Evolved Due Diligence: In our experience, traditional venture metrics alone are not sufficient for assessing a crypto startup’s potential. We take a broader approach, evaluating not just the balance sheets, but also the product-market fit, team capabilities, and regulatory standing.
The Regulatory Landscape: Understanding the constantly shifting regulatory environment is key to avoiding unforeseen pitfalls and ensuring the long-term sustainability of a startup.
Insight 2: Team Dynamics — The Human Factor in Success
We believe a company is as strong as its weakest link, which is often human capital. Cohesion, leadership, and commitment are harder to quantify than financials, but they’re no less critical. In this chapter, we dive into the qualitative traits we look for in a startup team and why these factors often make or break a venture.
Prioritizing Proven Leadership: We pay close attention to a founder’s history of leadership. Experience, especially involving both successes and setbacks, brings along a learning curve that we consider invaluable for navigating the often-turbulent crypto markets.
Emotional Investment: When founders are deeply invested in solving a problem, often because they’ve experienced it themselves, they bring an irreplaceable passion to the venture. This often translates into a more empathetic approach to both product development and customer experience.
Cohesion and Inspiration: We look for teams that display strong cohesion and the ability to inspire each other. In our view, a team that can work well together, especially under stress, is far more likely to overcome the inevitable challenges that arise in the startup journey.
Adaptability: In a field that’s constantly changing, we value teams that demonstrate the ability to adapt without losing sight of their core mission.
Insight 3: Assessing the Product — Where Opportunity and Innovation Intersect
In a crowded marketplace, differentiation is key. The product, therefore, needs to offer something unique while also addressing a clear need. This chapter unpacks the criteria we consider critical for a compelling product offering.
Identifying Market Gaps: We value products that not only solve a problem but also fill a noticeable void in the existing market. Meeting a previously unmet need or solving a problem more effectively than existing solutions captures our interest.
The Multi-Dimensional Role of Tokens: In the crypto world, tokens serve a variety of functions, from governance to utility. We’re particularly keen on projects where the token has a well-defined role and adds real value to the ecosystem, beyond just serving as a medium of exchange.
A Meticulous Competitive Analysis: It’s not enough for a product to stand out; it must also stand up against competitors. We look for startups that have a clear understanding of their competition and can articulate a solid strategy for differentiation.
Feasibility and Scalability: We give preference to projects that demonstrate a realistic and achievable roadmap for scaling their product or service.
Insight 4: Beyond the Basics — The Overlooked Facets of Due Diligence
In our experience, due diligence is not complete without delving into several often-overlooked areas. This chapter provides insights into these additional layers of analysis that help us make more informed investment decisions.
Market Scale and Potential: We look for startups that aim to serve a large Total Addressable Market (TAM), as this usually offers greater potential for growth and profitability. However, we balance this with the consideration of how achievable capturing this market really is.
Regulatory Compliance: Compliance is a strategic asset. Understanding the regulatory landscape is critical, not just to mitigate risks but also to identify opportunities that others may overlook due to regulatory complexity.
Cybersecurity Measures: Given the digital nature of crypto, a robust approach to cybersecurity is not just optional but fundamental to a startup’s viability.
Conclusion: Beyond The Initial Investment — A Continual Commitment to Partnership and Innovation
Our relationship with each investment extends far beyond the initial transaction. We view due diligence as a continuous commitment, aimed at fostering long-term partnerships and contributing to the rapid evolution of the crypto space. This short guide has been designed to demystify our nuanced approach to due diligence and to provide startup founders with valuable insights into what we’re looking for. We believe that this multifaceted evaluation is crucial for any venture aiming to thrive in the complex, ever-changing crypto landscape.
If you are a founder building something that aligns with these criteria and values, we wholeheartedly encourage you to reach out to info@breed.vc We’re committed to engaging with innovators and entrepreneurs who aim to shape the future of crypto!
The MEV Bible Part 2 of 2
A Journey into the Heart of Blockchain’s Decentralization Challenges and its Solutions.
A Journey into the Heart of Blockchain’s Decentralization Challenges and its Solutions.
Introduction
Welcome to Part 2 of the MEV Bible (Part 1 here), where we’re about to embark on a deep dive into one of the blockchains most intricate complexities, known as Miner Extractable Value, or our buddy, MEV. Now, you might be asking, “Why should I care about MEV?” Strap in, because it’s more than just a simple technical glitch. It’s a fascinating issue that catapults us right into the epicenter of the blockchain universe’s grand dilemmas around authority, equality, and the true spirit of decentralization.
Think of MEV as a wild creature, hidden within the intricate labyrinth of the blockchain ecosystem. It’s an unintended consequence of blockchain’s transparency and transaction sequencing. And while some may argue it’s an inherent part of the system, others warn it has the power to stir up some serious chaos.
The MEV Battle Continues
We’ll be exploring the arguments of those who view MEV as a cornerstone of the blockchain, and contrasting these with the views of those who see it as a nuisance that needs to be eradicated. We’ll shed light on why MEV could potentially morph into a monumental problem for the blockchain universe, and also bring into focus some innovative strategies aimed at taming this beast. These strategies range from auctions and cryptography to ensuring fair transaction ordering and even good old-fashioned regulation.
So, as we navigate this journey, the central question we’ll grapple with is whether we allow MEV to roam free, potentially jeopardizing the core principles of decentralization, or whether we channel our creativity to devise ways that empower users and foster a more equitable and inclusive crypto environment. The stakes are sky high and the outcome has the potential to reverberate across the entire blockchain cosmos. So let’s dive right in, shall we?
What’s the MEV Supply Chain?
So now that you understand what MEV is from part 1 of this series, let’s introduce the different actors in this ecosystem and how they interact with each other.
The picture above shows at a high level the current actors involved in the MEV industry today.
User — Anyone that wants to make a transaction on the Ethereum blockchain.
Wallet — An interface that the user utilizes in order to connect to the blockchain and send transactions through. To take Stephane Gosselin’s (from the above image) definition, a wallet in this instance also includes everything at the application layer: dApp UI, wallet, and smart contract protocol.
Searcher — These are the actors who are actually running various MEV strategies to profit from the sequencing or reordering of transactions.
Builder — Transaction aggregators that actually construct the block. Prior to PoS, this was the job of the miner while in PoS this is actually done by the validators. With regard to L2, this work is delegated to the sequencers.
Validator — Actors who validate and finalize blocks. Currently validators and builders are the same entity, but there’s ongoing research into separating them into two distinct roles.
When we look at the current system, Flashbots is clearly the leader in the MEV space. At one point, they even had over 90% of Ethereum miners using their services. The system that Flashbots built is essentially a version of Proposer/Builder Separation, which we’ll touch upon later on — for now, the picture below does a good job of depicting how block building happens.
Utopia or Dystopia?
Taking inspiration from Stephane again, centralization within the MEV supply chain can cause a blockchain to trend towards what he calls “Utopia” or “Dystopia.”
MEV or “Miner Extractable Value” can lead to two potential futures — a utopia or a dystopia, based on how it’s managed and developed.
A MEV Utopia would involve an open and fair system where everyone has an equal chance of benefiting from the reordering or inclusion of transactions. This would be a system where MEV is democratized, and no one player has an unfair advantage over others. Technical solutions would be created to ensure that all actors have an equal opportunity to extract MEV, preventing a small group from dominating the blockchain.
On the other hand, a MEV Dystopia would emerge if the control and benefits of MEV extraction are concentrated in the hands of a few. If powerful actors can exploit uneven access to information and manipulate transaction ordering for their own gain, it could lead to a system reminiscent of traditional finance, where retail investors often end up at a disadvantage. This could result in issues such as flash crashes, cascading failures, and censorship, hurting regular investors.
In essence, the outcome depends on how the crypto community addresses the issue of MEV. It can either lead to a fair and equal system (a utopia) or a system that favors the powerful and leaves regular investors at a disadvantage (a dystopia).
Understanding MEV: Two Different Views
Before we get into the problems and solutions to MEV, let’s first introduce two of the main of the philosophical underpinnings of MEV.
MEV is fundamental and should be democratized — MEV is not only a fundamental property of blockchain networks and it’s not going away.
MEV is detrimental and should be removed — MEV has no societal benefit and taking advantage of it is actually detrimental to the network participants.
Why is MEV Fundamental?
Auditbility — Users can check the status of the blockchain, which makes the network more open. But this checkability also means we can know what the results of actions will be, which can lead to bribing. Since results are decided by the order of transactions and validators can set this order, auditability can also lead to MEV in blockchain systems.
Interoperability — Different blockchain networks and systems can work with each other. But since each of these systems is built differently and has different trust levels, these differences can probably be sources of MEV for those who control the order of blocks.
Diverse Fairness Models — There’s no one-size-fits-all idea of fairness, and different models have different rules and work in different conditions. When there’s a mismatch between these models and conditions, it encourages certain versions of history, which lead to MEV.
Why is MEV Detrimental?
MEV is essentially a cost that validators put on users for no real reason, without the community agreeing to it, and without understanding what these costs mean for users.
There are ethical worries around MEV and front-running, which could make people see blockchain networks in a negative light and draw more attention from regulators.
Big MEV Problem Explained Simply
So, why is MEV a big deal for blockchain networks and why should you care? Well, as we said at the start, MEV could mess up blockchains’ ability to create systems that are fair, open, permissionless, and decentralized!
By now, it should be pretty clear that organizing transactions to make a profit can cause many problems and could stop blockchain networks from delivering on their promises. But there’s more — MEV can also threaten a blockchain’s ability to keep a permanent record of transactions. This is because as the rewards for creating new blocks decrease over time and more people use the network, there might be MEV opportunities that make more money for a validator than just creating a new block. In fact, some MEV opportunities could be so profitable, a validator might even try to change past transactions so they get the profits instead. That’s why MEV is a problem we really need to solve.
Don’t worry, there are already some clever people discussing this issue. Some of these solutions are already being used, while others still need to be looked into.
Possible MEV Solutions
Before we look at the possible solutions, it’s important to say that we don’t know yet if MEV can actually be completely solved. Some people, like the folks at Flashbots, think that it’s almost impossible to completely get rid of MEV. They believe the best solution is to make sure everyone has a fair shot at MEV to stop one group from controlling it all. Others, like Chainlink, think that MEV can be reduced a lot, to the point where it’s not worth it for people to take value from the blockchain system. We’re not going to argue about that here. We just want to help you understand what the different solutions might be.
There are four main types of possible MEV solutions: 1) Auctions, 2) Cryptography, 3) Fair Ordering, and 4) Regulation. Each of these have good and bad points, which we’ll talk about soon. We’ll probably need a mix of these solutions to really tackle the bad effects of MEV.
1. Auctions
Auctions are a simple way to handle the MEV issue. The basic idea is to let validators bid to get the chance to build a block.
This is the most common MEV solution being used right now, and here are the good and bad points of an auction-based MEV system.
Pros:
Efficient Price Discovery — Auctions can help find the right price because people compete to bid on things. In this case, those things could be 1) the chance to organize transactions and MEV opportunities, and 2) the chance to create blocks. This helps make sure things are priced correctly based on supply and demand, leading to better price stability and less volatility.
Transparency — Auctions are usually transparent, meaning everyone can see the prices others are offering. This helps build trust because everyone can see that the auction is fair and open.
Fairness — Auctions can be fair by giving everyone an equal chance to bid, no matter how big or small they are. This helps make sure everyone has a fair chance to get what they want.
Liquidity — Auctions can help make the market more liquid by providing a place for buyers and sellers to trade quickly and easily. This can help make the market more efficient by reducing transaction costs and helping find the right price.
Cons:
Market Manipulation — Auctions can be manipulated, especially if there aren’t many people participating or if some bidders have a lot of power. This can lead to distorted prices and make the market less efficient, which can hurt participants.
Limited Access — Not everyone might be able to participate in auctions, especially those who don’t have the resources needed (MEV is a very competitive and resource-heavy industry). This can limit the number of potential buyers and sellers, which can reduce market efficiency and liquidity.
High Transaction Costs — Auctions can be expensive, especially if there are auctioneers or other middlemen involved (it costs money to build the infrastructure and make sure it’s fair, transparent, and efficient). These costs can reduce profits and make people less likely to participate in auctions.
Limited Price Certainty — Auctions can be unpredictable, with the final price often being very different from early estimates. This can be a problem for both buyers and sellers who might not know the true value of what’s being auctioned, leading to uncertainty.
That being said, here are a few solutions that are being implemented, developed, and/or researched today that tackle MEV from an auction perspective.
Blink: Blink is developing a marketplace where searchers can bid on user transaction order flow and some of the profit will be sent back to the users.
BloXRoute BackRunMe: BackRunMe is a DEX solution for users created by BloXRoute that is integrated with Sushiswap and Uniswap. BackRunMe offers front-running protection by sending user transactions directly to validators while searchers share a portion of their back with the users.
DFlow: DFlow is Cosmos-based appchain that is building a decentralized orderflow marketplace to allow users to trade marketable order flow (unfulfilled buy and sell orders). Users can directly sell their orders to market makers, bypassing the typical MEV issues they run into on-chain.
Eden Network: Eden Network is another Flashbots like project that is building similar products. They have a private RPC endpoint for transactions, a place for searchers to submit bundles, and a place for builders to create blocks for validators.
Flashbots MEV-Boost: Flashbots is the leading MEV project and has developed their version of the Proposer/Builder Separation mechanic within Ethereum. Flashbots has created a marketplace for valuable blocks which is sourced from specialized builders and searchers. Over 90% of the validator market share is connected to MEV-Boost.
Flashbots Protect: Flashbots created an API that developers can integrate into their applications, which allows users to send their transactions through the Flashbots Network. There is also an RPC endpoint that users can connect their wallets with to send transactions to the FB Network.
Flashbots SUAVE: Flashbots initiative to further decentralize the MEV ecosystem. SUAVE stands for Single Unifying Auction for Value Expression and will attemp to unbundle the mempool and block builder role from existing blockchains.
Kolibrio: Kolibrio is another MEV solution that attempts to drive value back to the users. Kolibrio lets users, RPC nodes, and other transaction broadcasters submit transactions through a relay where the transactions are checked for MEV, which is shared back with the broadcaster.
Manifold Finance OpenMEV: OpenMEV aims to provide a credible neutral platform for facilitating both aggregation and direct communication channels between block validators, block producers and block synchronizers for the Ethereum and EVM-based networks.
Mekatek: Mekatek is building an open blockspace market for the interchain future, that enables expression of a rich set of preferences and to guarantee fee distribution to all parties in the value chain.
Proposer/Builder Separation: Ethereum currently allows block proposers/validators to choose transactions to include in blocks, which can lead to market manipulation and advantages for centralized pools. Proposer/builder separation (PBS) splits the block construction and proposal roles, with builders submitting bids for exec block bodies and proposers only accepting the highest bid.
Rook: Rook takes a slightly different approach to MEV by attempting to capture it at the application layer and then redistributing it back to the users who generated it. It does this through a coordination game whereby their Keepers (searchers) bid against other searchers in a zero-sum manner to disincentive MEV.
WallChain: Wallchain integrates with DeFi platforms and helps capture those profits, fully eliminating malicious bots. The captured profits significantly increases the DeFi revenue as well as helps provide users cashback.
2. Cryptography
Another way of dealing with MEV is through cryptography where the basic premise is the create some form of privacy around transactions via a commit and reveal scheme so that it’s more difficult for searchers, block builders, and validators to access MEV in the first place.
This also has its own advantages and disadvantages.
Pros:
Privacy — Cryptographic solutions can provide privacy, which can work well with auctions by letting participants privately submit bids and MEV transactions. This can encourage more honest bidding for MEV opportunities and help prevent “MEV stealing” and other exploitations. Privacy can also help mitigate MEV by hiding user transactions until a validator commits to adding them to their block, which would protect these transactions from MEV extraction altogether.
Fairness — Cryptographic solutions can also promote fairness in the MEV ecosystem. They can help verify the integrity of transactions and ensure they follow a pre-agreed set of rules. New cryptographic techniques, like homomorphic encryption, can also allow computations to be done on encrypted data without needing to decrypt it, which could prevent MEV altogether.
Cons:
Complexity and Cost — Cryptographic solutions can be complex and require a lot of technical expertise to implement and use effectively. This can be a barrier for smaller applications or protocols, reducing the number of MEV-resistant projects in the ecosystem and thus reducing competition too.
Vulnerabilities — Cryptographic solutions may introduce new vulnerabilities or attack vectors, especially if the cryptography is not well-designed or implemented correctly. This can increase the risk of security breaches or other types of exploits.
Some projects that are looking to tackle MEV through cryptography are:
Anoma: An intent-centric, privacy-preserving protocol for decentralized counterparty discovery, solving, and multi-chain atomic settlement. Anoma has been working on Ferveo, which is a protocol for mempool privacy using distributed key generation and threshold cryptography.
Fairblock: Fairblock is building a solution to combat bad MEV by using distributed Identity Based Encryption (IBE). IBE is a novel, secure, and efficient pairing-based scheme that can be used to enable pre-execution privacy. Users will be able to use FairBlock to send encrypted transactions and once an order is finalized, the transactions are decrypted and then executed.
Oasis Network: Oasis Network is a decentralized layer 1 blockchain solution designed to support confidential and private transactions and smart contracts, which can help mitigate MEV.
Secret Network: Secret Network is a privacy-preserving blockchain that enables “secret” smart contracts with encrypted inputs, outputs, and state. This means that they have an encrypted mempool, which helps to mitigate MEV.
Shutter Network: Shutter Network is an open-source project that aims to prevent front running on Ethereum by using a threshold cryptography-based distributed key generation (DKG) protocol.
3. Fair Ordering
Fair ordering solutions are a third way of trying to prevent MEV and are fairly straight-forward to understand. The idea is that the protocol itself will be able to order transactions in a fair way so that transactions aren’t able to be front-run or back-run.
Fair ordering also comes with it’s own set of pros and cons.
Pros:
MEV Mitigation — By ensuring a fair order to transactions, where no transaction can be purposely inserted before or after another, this can completely prevent searchers from consistently front-running or back-running users. This method has the potential to fully eliminate MEV.
Cons:
Complexity — Designing a fair distributed system can be complex and challenging, as there are many factors to consider and trade-offs to make. This can lead to delays and increased costs.
Subjectivity — Fairness can be subjective, and different stakeholders may have different opinions on what is fair. This can lead to disputes and challenges in implementing a fair system that is acceptable to all.
Scalability — A fair system might be more difficult to scale, as maintaining fairness across a large and growing number of participants can be challenging. This can lead to performance issues and increased costs as the system grows.
Fair ordering techniques to solve MEV are the most emergent solution of solving MEV. Here are a few projects that are being researched.
Aequitas: Aequitas are first consensus protocols that provide order fairness. It provides a leader-based and a leaderless protocol each for the synchronous and asynchronous settings, for a total of four protocols that all provide consistency, block-order-fairness, and some form of liveness.
Fairy: Fairy is a system that makes sure transactions in a distributed network are ordered fairly, so no one can cheat by changing the order based on who sent the request. It does this by using special computer environments called Trusted Execution Environments (TEEs) to protect the transactions and make sure they’re ordered correctly. Fairy is better than other similar systems because it also hides who sent the request, not just what the request is.
Helix: Helix is a way to make sure that transactions on a distributed network are fairly ordered. It does this by using encryption to hide information from the nodes that are ordering the transactions, which makes it harder for them to cheat. Helix also uses a verifiable source of randomness to choose which nodes get to order transactions, and it gives more power to nodes that have a good reputation for following the rules. This helps make sure that the system works fairly and efficiently.
4. Regulation
A less discussed method of mitigating MEV is simply good old fashioned regulation. Ban the act of front-running or back-running transactions or create higher tax implications for actors that participate in MEV.
That being said, this also creates costs and benefits that we’re all very familiar with.
Pros:
Consistency — Regulation provides a uniform set of rules that everyone must follow, reducing confusion and creating a fair environment.
Accountability — Regulation sets clear responsibilities and expectations for those participating in MEV, making it easier to hold them accountable for their actions.
MEV Prevention or Mitigation — Regulation can protect the public from MEV by setting standards or restrictions for transaction behavior, ordering transactions, bidding, front-running, etc.
Cons:
Costs — Regulation can be expensive to put in place, both for the regulators and those being regulated. Compliance can require significant resources, and the cost of enforcement can be high.
Inefficiency — Regulations can be rigid and slow to adapt to changes in the environment. They can also create unintended consequences or incentives that work against their intended goals.
Compliance Issues — Some regulated parties may try to avoid the regulations, either through legal loopholes or outright violations, leading to enforcement challenges and potential negative consequences.
Stifling Innovation — Overly strict regulations can suppress innovation, particularly in emerging areas where flexibility is important.
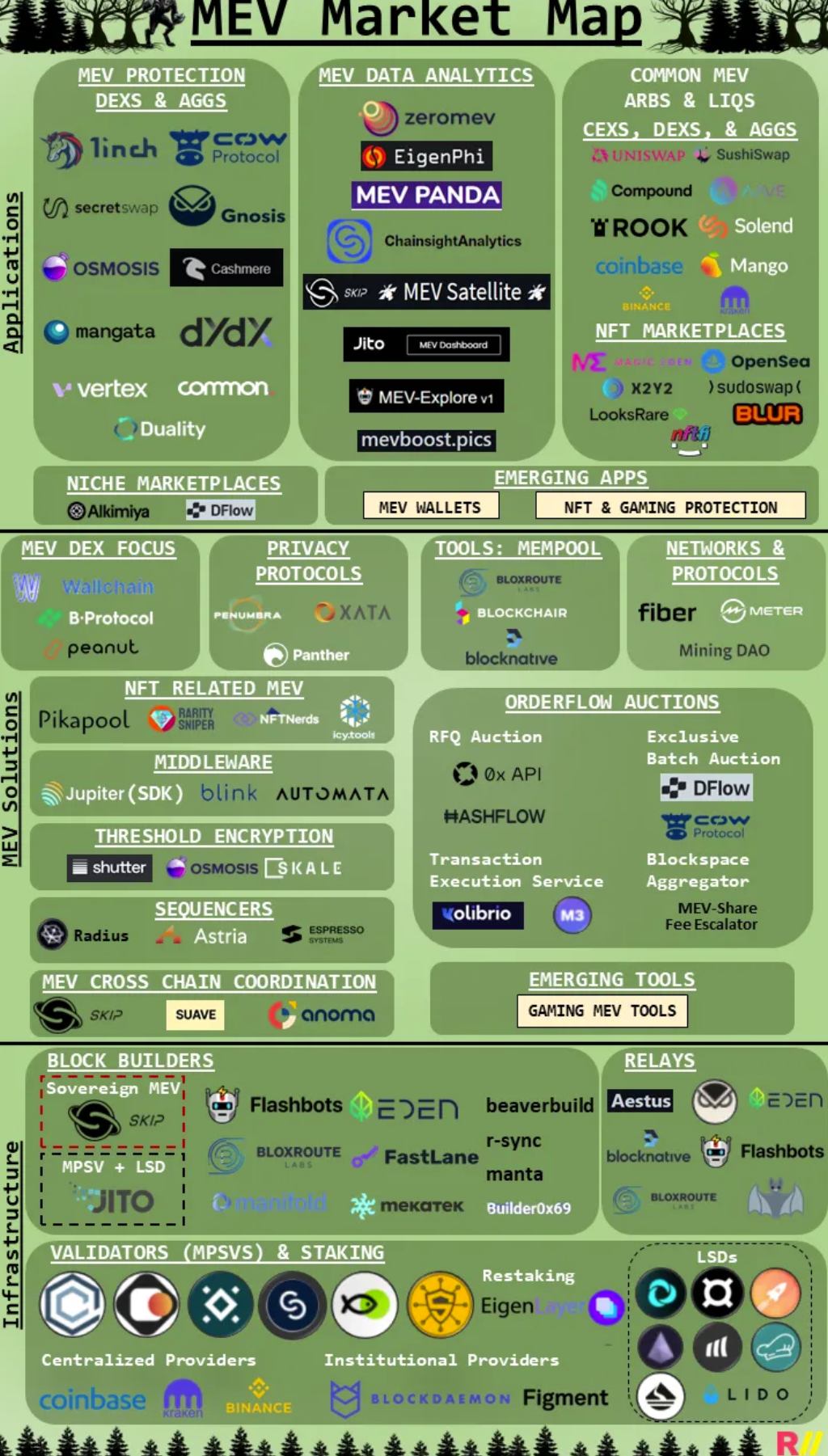
The companies that we listed above are only a select few out of the many that are trying to mitigate or solve MEV. Here’s a more holistic market map of the entire industry (kudos to AnalyticalAli for creating this amazing market map!)
MEV Market Map — All Credit Goes to AnalyticalAli
Conclusion
So, we’ve finally reached the end of our deep dive into MEV. It’s crazy, right? This isn’t just about the nuts and bolts of blockchain, it’s so much more. We’re talking big picture stuff, like who’s in charge, how we handle power, and what decentralization really means. MEV shows us the tricky balance between the chance for everyone to get involved and the risk of some folks taking advantage. It makes us stop and think about the give-and-take between fast and fair, being open versus keeping stuff private, and choosing between what’s good for one person and what’s good for all of us.
At the end of the day, what happens next with MEV is up to us, the blockchain community. Our choices will shape what decentralization looks like in the future. Do we let the allure of MEV sway us, risking the principles of decentralization? Or do we face the challenge head-on, come up with creative solutions that put users first, and work towards a crypto ecosystem that’s fair and inclusive? We don’t know how it’ll pan out just yet. But let us tell you, the stakes are high, and whatever happens, it’s gonna ripple out and have a huge impact.
The MEV Bible, Part 1 of 2
MEV, short for Miner or Maximal Extractable Value, is a term that has been around in the crypto world for some time now. While there is no universally accepted definition, we’ll define MEV as the total value that validators can extract by sequencing, altering, or censoring transactions at the expense of users.
MEV, short for Miner or Maximal Extractable Value, is a term that has been around in the crypto world for some time now. While there is no universally accepted definition, we’ll define MEV as the total value that validators can extract by sequencing, altering, or censoring transactions at the expense of users. The existence of MEV potentially threatens the ability of blockchains to create fair, transparent, permissionless, and decentralized systems, making it a critically important research topic.
The existence of MEV poses a significant threat to the foundational principles of blockchains, including fairness, transparency, permissionlessness, and decentralization. The concept of MEV was first introduced by pmcgoohan in a 2014 Reddit post, dubbed “Miner Frontrunning,” and later formalized in the groundbreaking paper Flash Boys 2.0 in 2019. MEV presents a considerable challenge for blockchains as high transaction fees incentivize validators to prioritize certain transactions over others, potentially causing systemic issues that hinder the network’s ability to reach consensus. This concern is not only highlighted in the Flash Boys paper but also alluded to in a 2016 research paper on Bitcoin by esteemed academics from Princeton.
Since then, MEV has come front and center as the explosion of DeFi (Decentralized Finance) and NFTs (Non-Fungible Tokens) created enormous profits for MEV practitioners and miners/validators. It has also stirred up significant amounts of controversy due to transaction censorship that is in line with OFAC rules post the Tornado Cash incident. While there’s no way to calculate the exact amount of MEV and transaction censorship within a network, estimates are that the lower bound of total MEV is worth over $680 million and the percentage of OFAC compliant transactions is around 42% as February 28, 2023.
The aim of this primer is to provide you with a comprehensive understanding of MEV on Ethereum and evaluate current and potential solutions. As MEV is a complex and interdisciplinary topic, we will start by introducing fundamental concepts related to transactions and block production, which will form the basis for understanding MEV. We will then delve into the concept of MEV, its possibility, and the different types of MEV that exist in the ecosystem. We will examine MEV from a philosophical perspective, highlight its benefits and drawbacks, and conclude with an overview of potential solutions and their advantages and disadvantages.
Should MEV be fought or embraced?
Core Concept: Transactions and Block Production
In Ethereum, transactions are broadcasted to a network of computers or nodes that store the transaction in their local¹ mempools, where the transaction waits until a node validates it and commits it to a block on the blockchain. A mempool is a list of pending transactions that have not yet been included in the blockchain and each node has its own unique mempool to manage.
¹In the context of this discussion, “local” refers to data that is stored on a specific node or computer rather than on the blockchain itself. For example, when you store something on your computer’s hard drive, it is considered local to your computer. It’s important to note that each computer or node has its own mempool, which is essentially a list of unconfirmed transactions, and these mempools are unique to each node. THERE IS NO UNIVERSAL MEMPOOL THAT ALL NODES SHARE!
Ethereum Transaction Lifecycle:
A user will initiate a transaction from a dApp or wallet, such as sending funds to another account or contract.
The user will then sign off on that transaction with their wallet, using their private key.
The wallet will then send the signed transaction to a node to get it onto the Ethereum network. A node is just a computer that is part of the Ethereum network running software that can verify blocks and transaction data.
The node will verify the transaction to ensure that it’s valid, set the transaction’s status to ‘Pending’, include in it’s own unique mempool, and then broadcast the transaction to it’s peers (other nodes that it’s connected to) — the verification process checks for a number of things and this step #4 also happens over and over again each time a node receives a transaction, which is how transactions are propagated through the network.
Now that we have some idea for how transactions are verified, stored in mempools, and propagated across the network, we can dive into the validation process to get a better understanding of how blocks of transactions are produced and included in the blockchain.
While the transaction lifecycle is taking place, the block producing process is also happening simultaneously.
Users who want to validate transactions have to run a node and stake 32 ETH as collateral with that particular node — these nodes are also known as validating nodes or validators. A user can operate multiple validators but must stake 32 ETH with each one. The reason for posting this collateral is to protect the network since some or all the collateral will be destroyed if a validator behaves poorly. We won’t get into what can cause the collateral to be slashed, but if you are curious, you can read more about that here.
During the block production process, the Ethereum network will randomly select a validator to propose a block. Once chosen, the validator will batch a set of transactions from their mempool (remember validators are just nodes that have 32 ETH worth of collateral posted), execute them and determine a new state for the network. The validator will then wrap all this information into a block and pass it to other validators in the network who will vote or ‘attest’ to the block. These other validators will re-execute the transactions in the block to ensure they agree with the proposed change to the global state. Assuming the block is valid they add it to their own database. This process of batching transactions into a block and proposing that block to be voted on by other validators happens every twelve seconds. If a validator hears about two conflicting blocks for the same slot they use their fork-choice algorithm to pick the one supported by the most staked ETH.
Now that we’ve gotten a good grasp for how transactions are propagated through the network and how transactions are actually included in the final blockchain, we can begin to explore what MEV is.
MEV Overview
What is MEV?
Like everything else in crypto, MEV is a fairly nascent field that is still relatively under-researched. There are multiple definitions of MEV depending on who you talk to, but for the purposes of this primer, we’ll stick to our definition of what MEV is — The total value that validators can extract by sequencing, altering, or censoring transactions as well as the profit they receive from transaction fees and block rewards.
Why is MEV possible?
The mempools are public, meaning anyone can look at pending transactions and see which ones are profitable
Validators proposing a new block have full control over which transactions to include and the order of transactions
These two facts mean that validators can effectively look into the mempool and sequence, alter, or censor certain transactions in order to generate a profit. We’ll dive into some specific examples in the following section.
Types of MEV
This value accrued to validators can be further broken into harmless and harmful profits.
Harmless MEV: These sources of revenue occur regardless of sequencing, reordering, or censoring transactions
Transaction Fees — Fees paid to validators for getting transactions included in the block.
Block Rewards — Validators receive rewards for attesting to blocks inline with the majority of other validators, proposing blocks, and participating in sync committees.
The validators earn these fees regardless of their ability to manipulate transactions so they can be considered neutral or harmless MEV.
Harmful MEV²: These sources of revenue occur because of sequencing, reordering, and transaction censorship.
Arbitrage — Taking advantage of price discrepancies across the crypto ecosystem, e.g., buying ETH at $1100 on one trading venue and selling it for $1200 on another. One could argue that some types of arbitrage have a neutral impact since price discrepancies have to be closed anyways, but one could also argue that MEV participants create an environment that does not incentivize competitive arbitrage strategies, which could lead to less efficient markets since MEV and arbitrage require different skillsets — for example, there’s a math competition where the first person to solve the problem wins, you and your friends are honest mathematicians but you are competing against opponents who can simply copy your answer and then pay a higher fee to turn it in first. While you and your friends are optimizing for math knowledge to solve these problems, your opponents are actually optimizing for the ability to copy your answer and turn it in first. These two skills are unrelated and this scenario might result in less incentive for the math-smart wiz kids to participate in these competitions.
Front-Running — When a transaction is inserted before another transaction in order to generate a profit, usually at the expensive of another user. It’s fairly obvious that this type of behavior is harmful and an example could be if a validator sees a profitable arbitrage transaction, copies it and executes the transaction themselves, and then places their transaction ahead of the original one.
Back-Running — When a transaction is inserted right after another transaction in order to generate a profit. This one is less obviously harmful, but when paired with a front-running transaction it becomes one of the most malicious types of MEV, a sandwich attack. Back-running can seem like front-running at times since the two are very similar and an example of a back-running strategy would be for a validator to wait for the deployment transaction of a hot NFT collection and then place their transaction right after to mint all the NFTs.
Sandwiching — When there is a front-running transaction and a back-running transaction that sandwich a users transaction between them. This is one of the most malicious types of MEV and is purely harmful, the classic example is Alice makes a transaction to purchase 1000 units of Token A on a DEX but sets her slippage too high, a validator could front-run Alice’s transaction by purchasing 1000 units of Token A to drive up the price, Alice would then purchase her tokens at a higher price, and the validator would then back-run that transaction and sell their tokens after, profiting off of Alice’s slippage and causing her to overpay for her tokens. If you have ever traded on a DEX, there’s a high chance that you have been sandwich attacked.
Censoring — When a transaction or a set of transactions are omitted from inclusion. This is another one of those fairly malicious types of MEV that is purely harmful. There’s a number of reasons why censorship is bad, first and foremost because the act of censoring transactions goes against everything decentralized blockchain networks stand for. We’ll use a liquidation event as an example here, where the price of an asset drops sharply and some on-chain loan is going to default. The borrower attempts to add more margin to their account but the validator proposing the new block purposely omits this transaction and places their own transaction to liquidate the position, causing the borrower to default and allowing the validator to purchase the assets at a significant discount.
²One caveat here is that the majority of profits coming from this category are not necessarily accruing to the validators, but rather professionalized arbitrageurs and other MEV participants. However, we categorize these as MEV since the validator could decide to run these strategies themselves.
Hopefully by now, you have some basic understanding around the block building process, the power that validators have in the network, and the problems that MEV can cause for users. In Part 2 of this MEV piece, we’ll dive deeper into the ecosystem, introduce the the actors in the MEV space and talk about some potential solutions.
Introducing Breed VC
A decade ago when I first started in this industry as a bedroom miner, I remember one day watching a Youtube video by Andreas Antonopoulos. This video introduced the concept of blockchain technology being applied to all other transactional applications outside of money.
Today, I am proud to announce the launch of Breed Fund I, a $20M pre-seed/seed crypto venture fund devoted to advancing the decentralized world.
A decade ago when I first started in this industry as a bedroom miner, I remember one day watching a Youtube video by Andreas Antonopoulos. This video introduced the concept of blockchain technology being applied to all other transactional applications outside of money. Bitcoin had already opened the world to an open financial system and this was just the first app!
A few months later a whitepaper dropped for a smart contract blockchain called Ethereum. After reading that whitepaper in 2014 I’ve been hooked on the idea of this fundamental change on how we interact ever since. I could see a new internet being born and the societal impact it will have.
It’s been quite a journey since then. I’ve now been through three bull/bear cycles and each time the size and impact of crypto increases. This cycle in particular saw the beginnings of true institutional acceptance, the rise of DeFi and NFTs.
Throughout these cycles, builders with conviction stay to push the industry forward and the tourists go home to lick their wounds. Now is the best time to build. The technology continues to accelerate and new use cases that will apply to not just hardcore crypto natives are on the horizon. The complexities of blockchain are starting to disappear and the real value of decentralization is being demonstrated. Everything will eventually be on the blockchain. It’s just a matter of when.
It’s Always Darkest Before the Dawn
I’ve created Breed VC to take the long term view no matter what market conditions we see. Crypto is here to stay and we plan to take an active part in helping builders create the top companies in the space.
Breed VC is backed by some of the top crypto-native investors & builders in the space. I’d like to thank all of my investors for joining me on this ride. These included investors out of Castle Island Ventures, Tribe Capital, Shima Capital, early employees from Uniswap, Figment, Circle and an array of other crypto-natives. We’ve built a vast network of the most value-add operators in the space and can’t wait to bring in new founders.
As a founder/operator who has built businesses, launched multibillion dollar crypto projects, and a power user of crypto applications, Breed VC provides a unique value set to our founders as they build the future.
Sincerely,
Jed
Come join us: Breed VC, Breed VC Twitter, Coindesk Coverage